Laura runs AI strategy at a mid-size software company, and she has a good problem. Her teams are excited about AI. Product managers are connecting copilots to Jira and Confluence through MCP servers. Sales reps are wiring up CRM integrations. Support engineers are pulling from knowledge bases in real time. The Model Context Protocol has made it remarkably easy for anyone to plug third-party services into their AI workflows — and her people are doing exactly that.
The trouble is, nobody told Laura.
The Ungoverned MCP Explosion
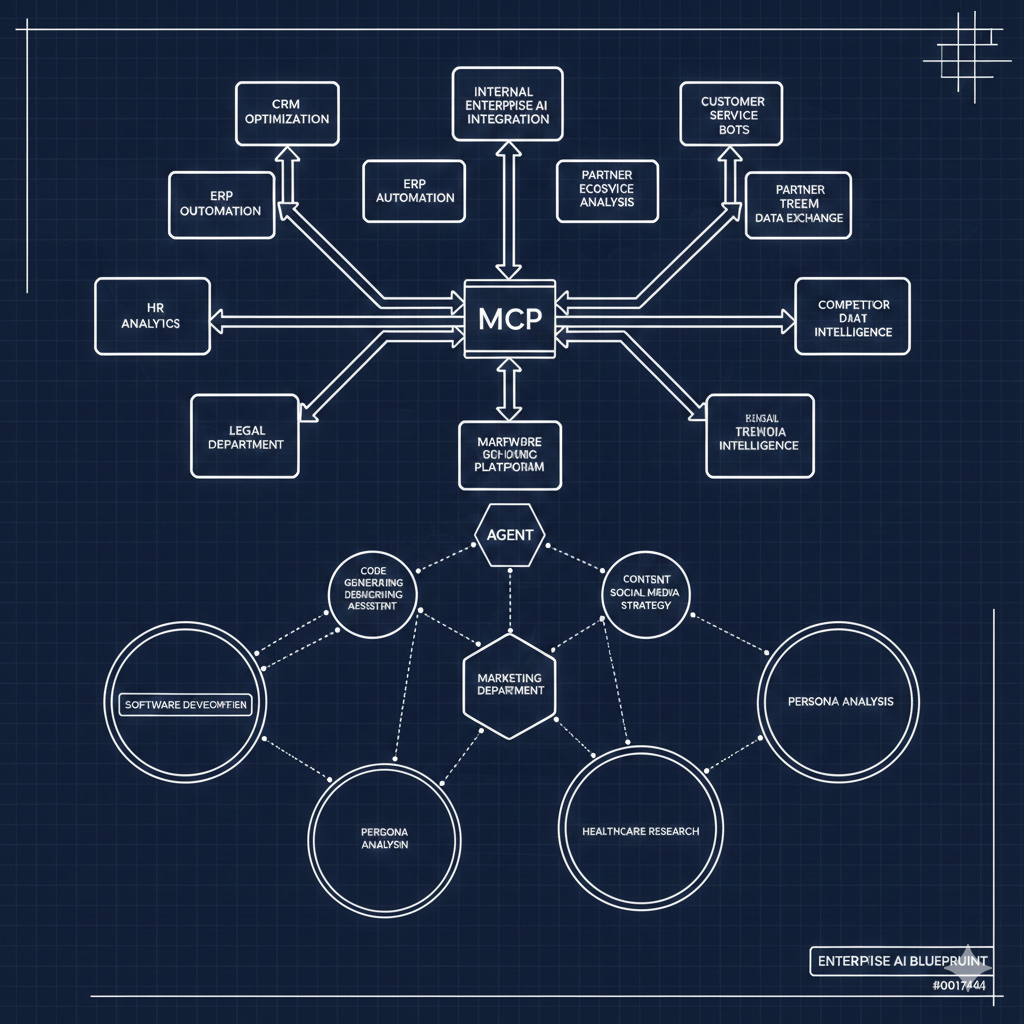
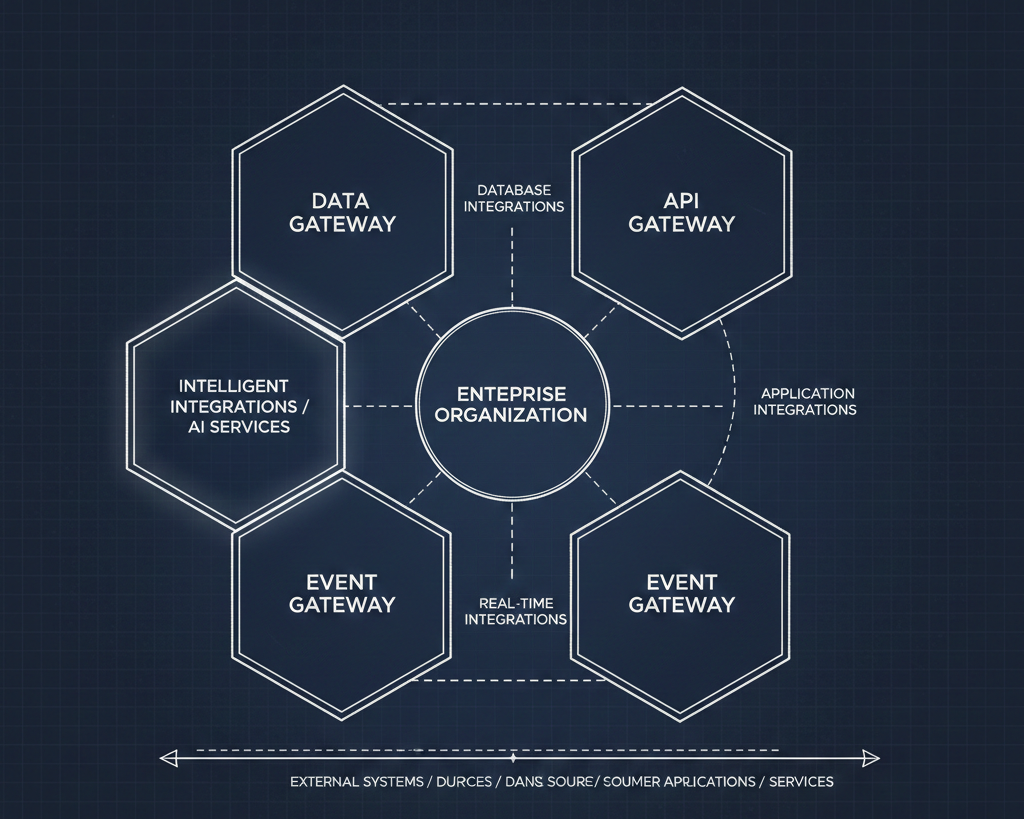
MCP servers have become the connective tissue between AI copilots and the external services teams rely on every day — think project management tools, communication platforms, cloud storage, analytics dashboards, and dozens of SaaS products. The protocol is powerful precisely because it's accessible: a team can stand up an MCP server, authenticate with a third-party API, and start feeding context into their copilot in an afternoon.
That accessibility is also the risk. Across most organizations adopting AI today, third-party MCP server usage is growing organically, team by team, with no central visibility into what's being connected, how credentials are being managed, or what data is flowing where.
Laura's situation is far from unique. It's becoming the default.
What "Ungoverned" Actually Looks Like
When there's no common framework for discovering, onboarding, and authenticating with third-party MCP servers, the consequences tend to surface in three places.
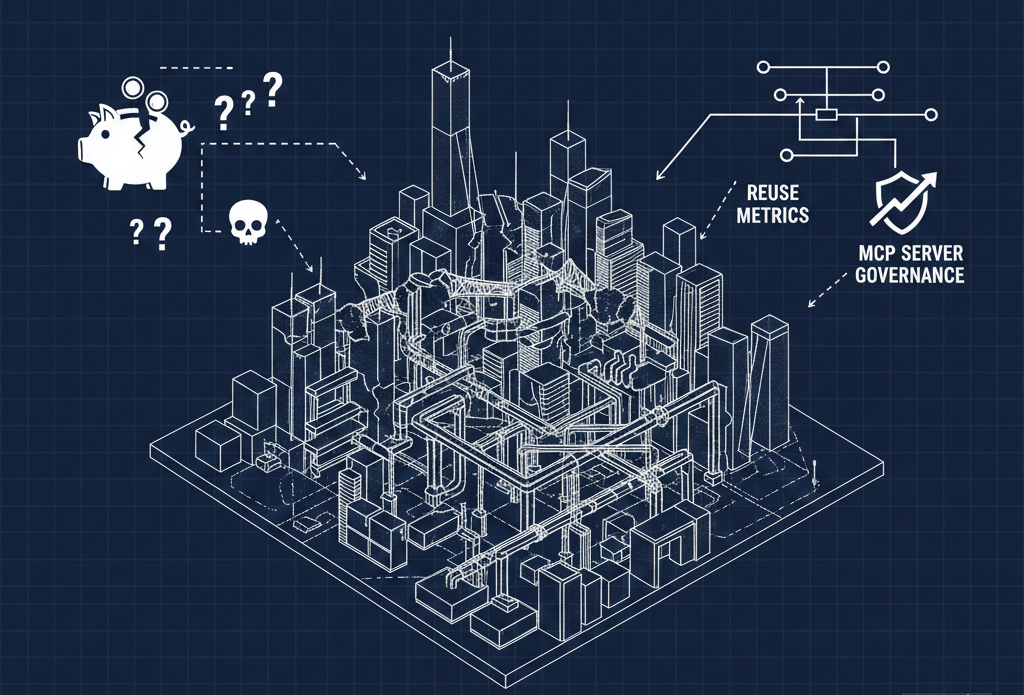
Security and privacy exposure. Every MCP server connection is an integration point — and every integration point is an attack surface. When teams independently configure access to external services, API keys get stored in local config files, OAuth tokens go unrotated, and sensitive data passes through connections that no one on the security team knows exist. A single misconfigured MCP server can expose customer data, internal documents, or proprietary workflows to an external service without any audit trail.
Uncontrolled costs. Third-party services accessed through MCP servers aren't free. Many charge per API call, per seat, or per volume of data processed. When a dozen teams are independently spinning up connections to overlapping services — or when a copilot makes hundreds of API calls in a single session — costs accumulate in ways that don't show up in any central dashboard until the invoice arrives.
Compliance gaps. Regulated industries have clear requirements around data handling, vendor management, and access controls. Even outside regulated sectors, most organizations have internal policies about which tools are approved and how data should flow between systems. Ungoverned MCP server usage bypasses all of it. If Laura can't tell you which third-party services her teams' copilots are talking to today, she certainly can't certify that those integrations meet compliance requirements.
Why This Keeps Happening
It's tempting to frame this as a discipline problem — teams going rogue with unsanctioned tools. But that misses the point. The teams connecting MCP servers to third-party services are usually trying to do their jobs better. They're not circumventing governance on purpose; there's simply no governance to follow.
Most organizations haven't yet built the infrastructure for governed MCP usage because the pattern is so new. There's no internal registry of approved MCP servers. No standard onboarding flow for connecting a new third-party service. No centralized authentication layer that enforces credential management policies. No usage monitoring that ties MCP server activity back to cost centers or compliance controls.
Without these building blocks, even well-intentioned teams have no choice but to figure it out themselves.
What a Governed Approach Looks Like
Getting ahead of this doesn't mean slowing adoption down. Laura doesn't want to kill the momentum her teams have built — she wants to channel it. A governed approach to third-party MCP server usage typically includes a few key capabilities.
A central registry for discovery. Teams need a single place to see which MCP servers are available, which third-party services they connect to, and whether they've been reviewed and approved. This eliminates the duplication problem — where three teams independently build connectors to the same service — and gives security and compliance teams a clear inventory of what's in play.
Standardized onboarding and authentication. Instead of each team managing their own API keys and OAuth flows, a governed approach routes authentication through a central layer. Credentials are stored securely, rotated on policy, and scoped to the minimum permissions required. New MCP server connections go through a lightweight review process rather than appearing unannounced in production.
Usage monitoring and cost attribution. Every call made through an MCP server should be observable — which team initiated it, which service it hit, how much data moved, and what it cost. This gives finance teams the data they need for budgeting, gives security teams the signals they need for anomaly detection, and gives Laura the visibility she needs to understand how AI is actually being used across the organization.
Policy enforcement. Governance without enforcement is just a suggestion. The system needs to be able to block unapproved MCP servers, flag connections that violate data handling policies, and alert on unusual patterns — all without requiring a human in the loop for every routine connection.
The Cost of Waiting
Every week that goes by without a governed approach is another week of accumulated risk. More unmanaged credentials in the wild. More cost surprises at the end of the quarter. More integration points that no one on the security team can account for.
The organizations that will get this right are the ones that treat MCP governance not as a restriction on innovation, but as the infrastructure that makes sustainable innovation possible. Laura's teams are already building the future of how work gets done. The question is whether the organization is going to build the guardrails before or after something breaks.
For leaders like Laura, the path forward is clear: make it easier to do the right thing than to do the ungoverned thing. Give teams a curated catalog of approved MCP servers, a painless onboarding experience, and the confidence that security and compliance are handled. Do that, and you don't just reduce risk — you accelerate adoption.
That's the governed approach. And it's how you turn a good problem into a genuine competitive advantage.